With the threat landscape littered with companies that don’t take their IT security seriously, it's hardly surprising that many are embracing what's known as a zero-trust policy to fortify their security measures. What exactly does zero-trust entail, and why does it prove so formidable in thwarting potential risks for your enterprise? Let's delve into this topic in today's blog post.
IT Solutions Network Blog
Oftentimes, a technology issue has less to do with the technology itself and more with the one using it. User error is simply one of the biggest reasons why technology support is asked for, and it’s such a common occurrence that it leads to many users becoming the butt of jokes among IT workers. People who provide IT support must practice empathy and understanding rather than foster this antagonistic mindset amongst teams.
Let’s face facts: regardless of how one spends their time at home, there really is no reason the vast majority of today’s workers would ever need the Xbox Game Bar application on their work device… and yet, there it is. Thanks, Microsoft?
This is an example of what is known as “bloatware”—unwanted software added to an operating system to help the developers, oftentimes to make a few extra bucks.
The decision to outsource your company’s IT decisions to a managed service provider is significant, and the importance is not lost on us. After all, you're essentially handing over the keys to your company's assets and resources, and it's crucial to ensure you make the right choice for the future of your business. Fortunately, gauging the suitability of a managed service provider can be made much easier by asking three key questions.
One of the most effective ways to reduce cyber risks is through comprehensive employee cybersecurity training. You protect your organization by ensuring that your workforce has the knowledge and skills needed to identify and thwart potential threats. Here are five essential considerations for implementing successful employee cybersecurity training programs.
With so many new and emerging threats to worry about in today’s cybersecurity landscape, it’s no wonder that some businesses and employees might be operating from a knowledge deficit regarding network security. We’re here to change that with a quick overview of the three biggest overarching threats your business must face and prepare for.
Scams using online retail giant Amazon have become more frequent around the holidays as online purchases tick up. Most of these scams come in the way of impersonation scams. With the holidays upon us, we thought we’d go through what kind of Amazon scams you should look for and how to avoid being a victim.
Managing a business poses considerable challenges, with a myriad of tasks demanding attention daily just to sustain the status quo. If you want to have a workforce that is not just present but genuinely invested in the enterprise, you will need to actively do more than just go through the motions. The question then becomes: How can one cultivate such dedication? This month, we will take a look at that very question.
With the holiday season upon us and online shopping surging, instances of scams targeting the popular e-commerce platform Amazon have become increasingly common. The majority of these scams involve impersonation tactics, posing a significant threat to unsuspecting users. With the festive season underway, it's crucial to be aware of the types of Amazon scams prevalent and take measures to avoid falling victim to them.
Cyberattacks are horrifically dangerous to any business, especially for small ones that might not have the resources to protect themselves with top-dollar solutions or preventative solutions to bounce back afterward. Today, we want to explore what really causes cyberattacks and how even slight changes to behaviors and situations can be indicative of danger.
Using the right technology can streamline operations, enhance customer engagement, and boost overall productivity. Despite its potential benefits, many small businesses often make significant mistakes when it comes to technology implementation. Let’s explore some of the biggest technology blunders small businesses make and how to avoid them.
Data is commonly regarded as one of a business’ most valuable resources. As such, it is critical that you protect it from threats of all kinds, including data leaks. Data leaks are nothing to take lightly, as their impacts range from a serious hit to your business’ reputation to an equally serious hit to your business’ finances. Obviously, this is something to be avoided, so let’s discuss how you can do so.
Today’s business leans on collaboration more than ever. Employees that work together efficiently and effectively can streamline processes and create a lot of positive momentum for a business that includes enhancing productivity and fostering innovation. Let’s go through a few variables that fuel solid collaboration.
We’ve all found ourselves in a pickle due to a dead smartphone battery, and if not, you’ve been living with a charger perpetually on your person. What is it that kills a smartphone’s battery so quickly?
As it turns out, a lot of things impact your smartphone’s capability to hold and maintain a charge over time. Let’s run through the list of factors that you could encounter, and how you can address them.
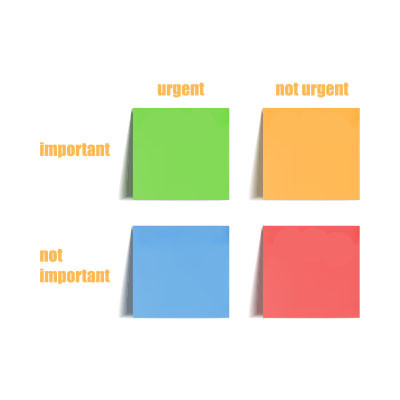
The modern worker has a lot of challenges and one of them is a laundry list of tasks to accomplish. For this reason, it’s best to have a plan for tackling your to-do list. One of the most effective ways to prioritize tasks is through what is called the Eisenhower Matrix. Inspired by a speech given by the former President of the United States and the Supreme Commander of the Allied Expeditionary Force in World War II, the Eisenhower Matrix simplifies complex task lists to make getting through them more effective. Let’s take a look at how it works.
The IT infrastructure of any business can be complicated, especially if you’re going about things the right way. In fact, managing your technology is, more often than not, a full-time job that needs to be fulfilled in order to be done appropriately. Let’s go over some of the key parts of managing and maintaining a business IT infrastructure, and while we cover these tasks, ask yourself if you’re 100% confident that they are happening for your business.
Look, we know that thinking about disasters can be a nerve-wracking experience, but you need to acknowledge that your organization is constantly in danger of becoming subverted by challenges outside your control. While you might not be able to stop a disaster from striking, you can be prepared for when it does strike, as well as how you respond to it. Let’s go over some of the methods you can use to ensure you have a plan in place.